Security Settings
Table of contents
Improving components security
Elqano is using Azure Firewalls to add extra layers of security.
The only IP addresses which will be allowed to access components (except for the web application) are the ones of the web application which is protected by a fully secured authentication.
Postgres
Apply the firewall rules to the postgres database.
Once the Azure App Service is up and runing, navigate to the Properties menu (in the left menu).
On this page, copy the Additional Outbound IP Addresses value.
Open the Custom deployment service of Azure and select Build your own template in the editor
Copy the following template in the editor and click on the Save button.
Select, the subscription, the Resource Group and the Location
Provide the following parameters
(Copy them in a safe place, they will be useful for the next steps of the process)
| Parameter | Action |
|---|---|
| Server_postgres_name | Name of the PostgreSQL server |
| Outbound_ip_addresses | Ip addresses copied from the App service |
- Accept the terms and click on
Purchaseand wait for the end of the creation process.
The list of whitelisted IP will be assigned to the database instance.
Redis
Apply the firewall rules to the Redis Server.
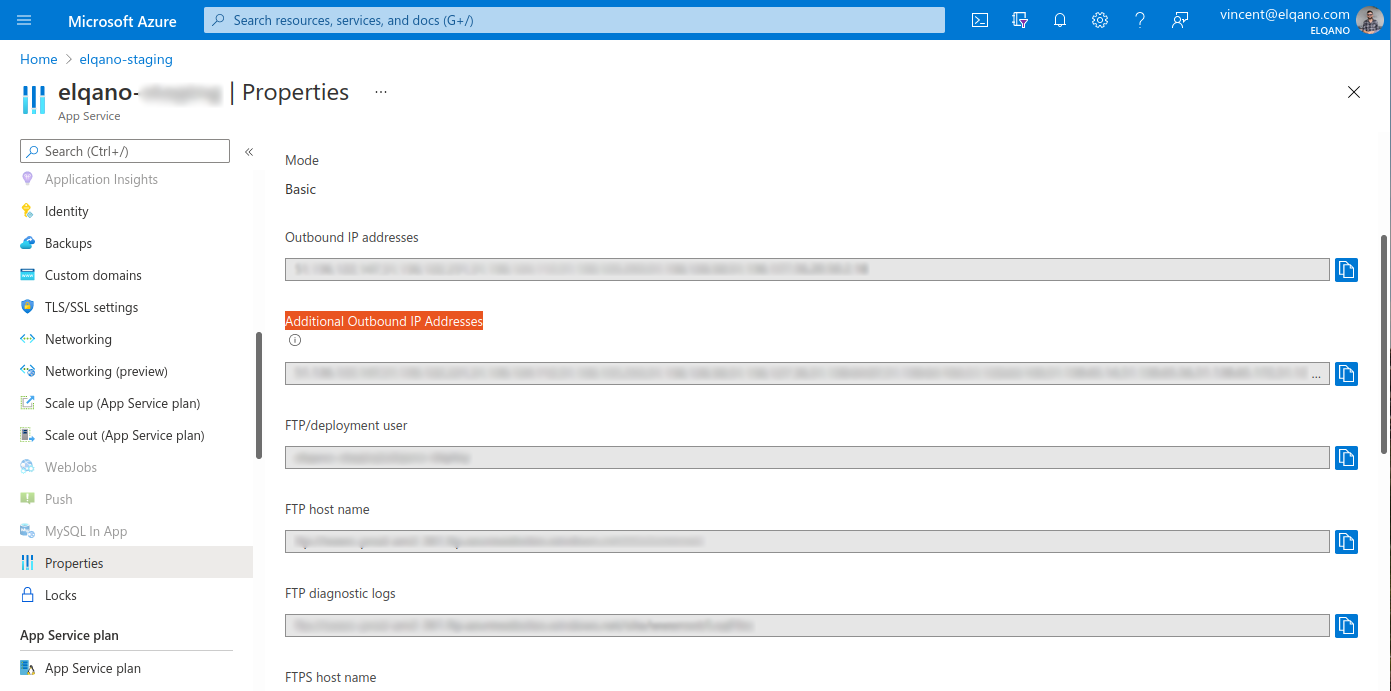
Once the Azure App Service is up and runing, navigate to the Properties menu (in the left menu).
On this page, copy the Additional Outbound IP Addresses value.
In your Redis Server, go to the Firewall section 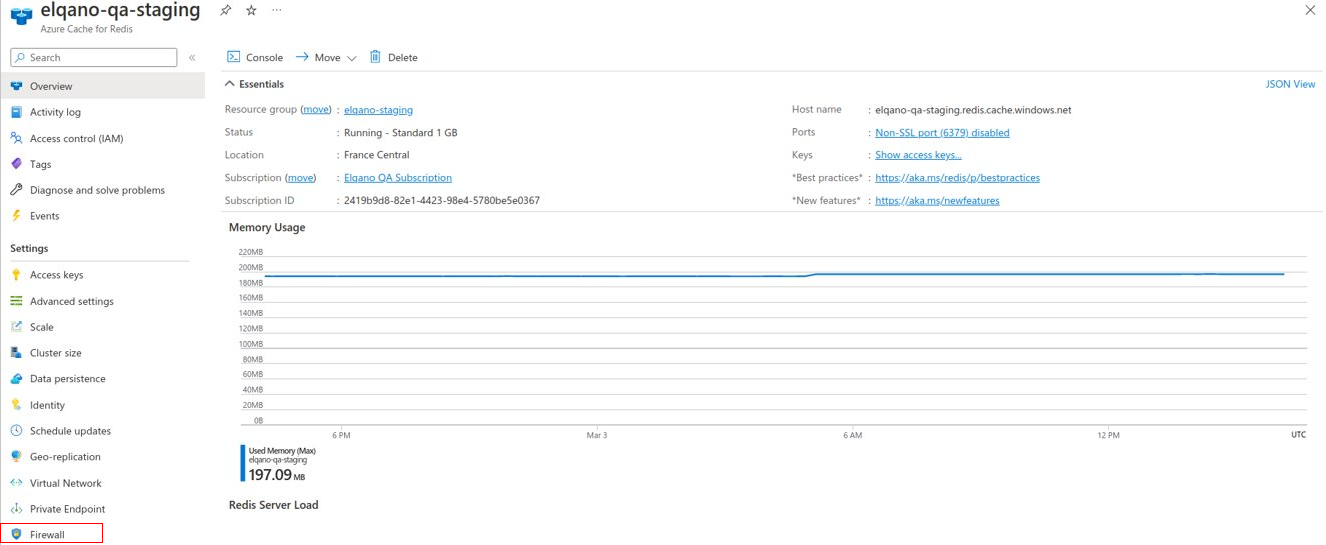
Add all the outbound IP Addresses and save the modifications: 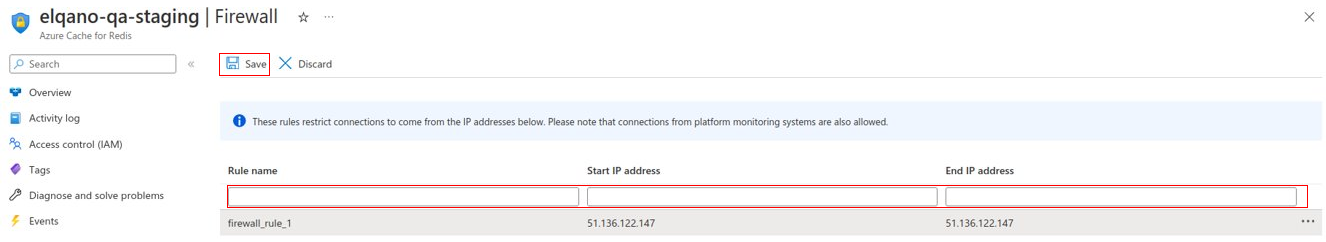
Elastic Search
Apply the firewall rules to the Elastic deployment.
Once the Azure App Service is up and runing, navigate to the Properties menu (in the left menu).
On this page, copy the Additional Outbound IP Addresses value.
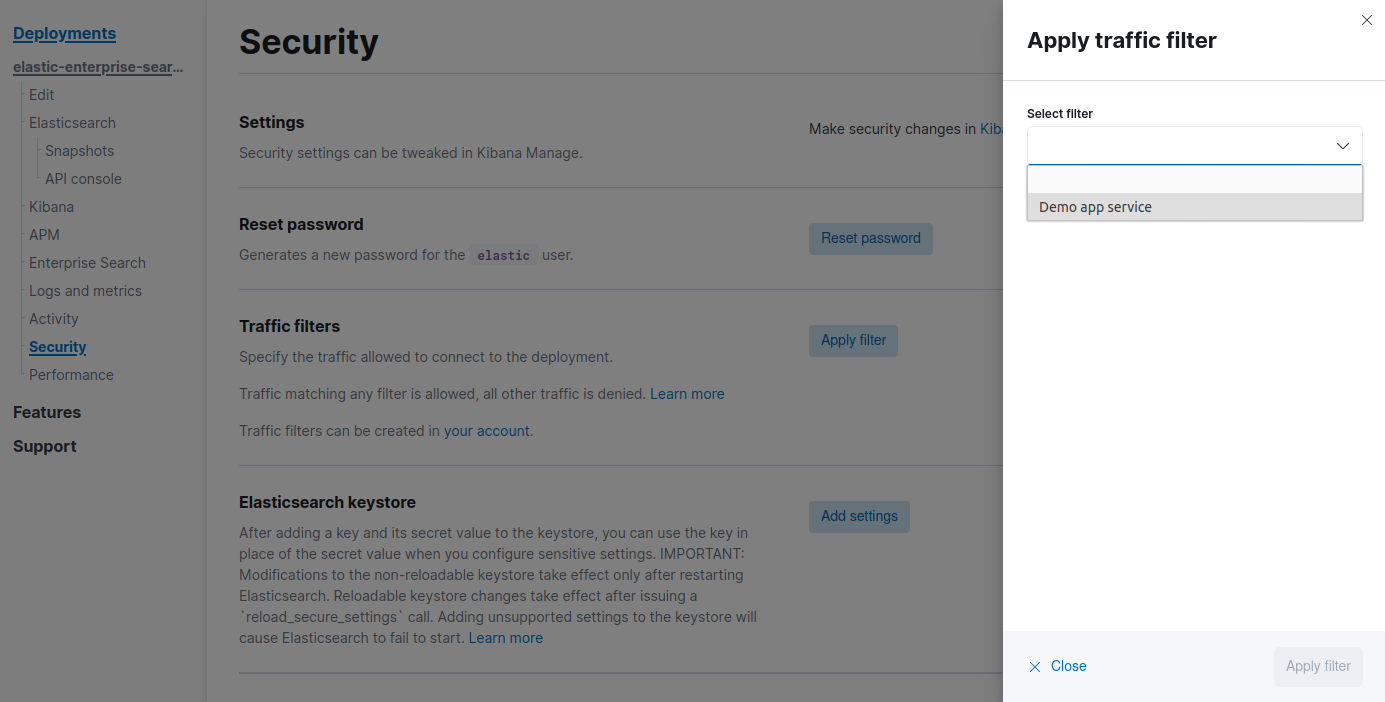
In Elastic Cloud, go to the Traffic filters page
Create a filter of type IP filtering rule set, name it, select the region in which your Azure app service is located.
Add one rule per IP from the Outbound IP address list and click on Create filter.
Once saved, navigate back to the ElasticSearch deployment, select the Security item on the left menu and apply the newly created traffic filter.
Azure Storage
Please note that if you want to add a firewall between the azure storage and the web application, you will need to use two distinct locations as communications between the two components are internal and do not use outbound IPs should the two resource be located in the same datacenter.
Please also note that adding a firewall between the two components disable the following features:
- the upload from computer feature
- the download of usage reports for admins if no VPN system is used (and the corresponding allowed IPs shared).
Indeed reports are stored in the azure storage as are uploaded-from-computers documents and the user will be denied access without an authorized IP address.
Apply the firewall rules to the Azure Storage.
Once the Azure App Service is up and runing, navigate to the Properties menu (in the left menu).
On this page, copy the Additional Outbound IP Addresses value. Add to these IP Addresses the IP ranges of your users’ VPNs.
In your Azure Storage, go to the Storage networking section 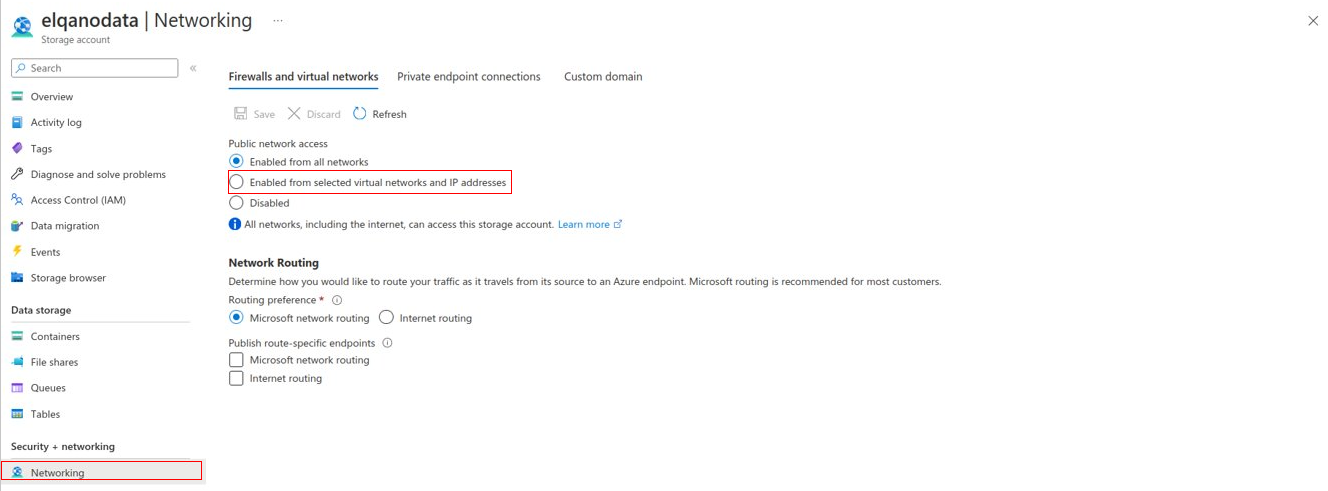
Add all the outbound IP Addresses and save the modifications:
